Enumeration with Nmap
Pentesting-Ports

Table of Contents
- Enumeration with Nmap
- Identify open ports with Nmap
- TCP Enumeration
- UDP Enumeration
- Directory and file search
- Relevant information search
- SSH brute force
- DNS brute forcing
- Obtain a copy of the configuration from a poorly configured CMS
- Versions and possible vulnerabilities
- Enumerate users on SMB
- WordPress enumeration
- HeartBleed attack
- Banner grab
- Check if vulnerable to shellshock
- Port Scanning
Nmap
Identify open ports with Nmap
Here is a graphic representation of what happens when we launch the different scans and how the communication works
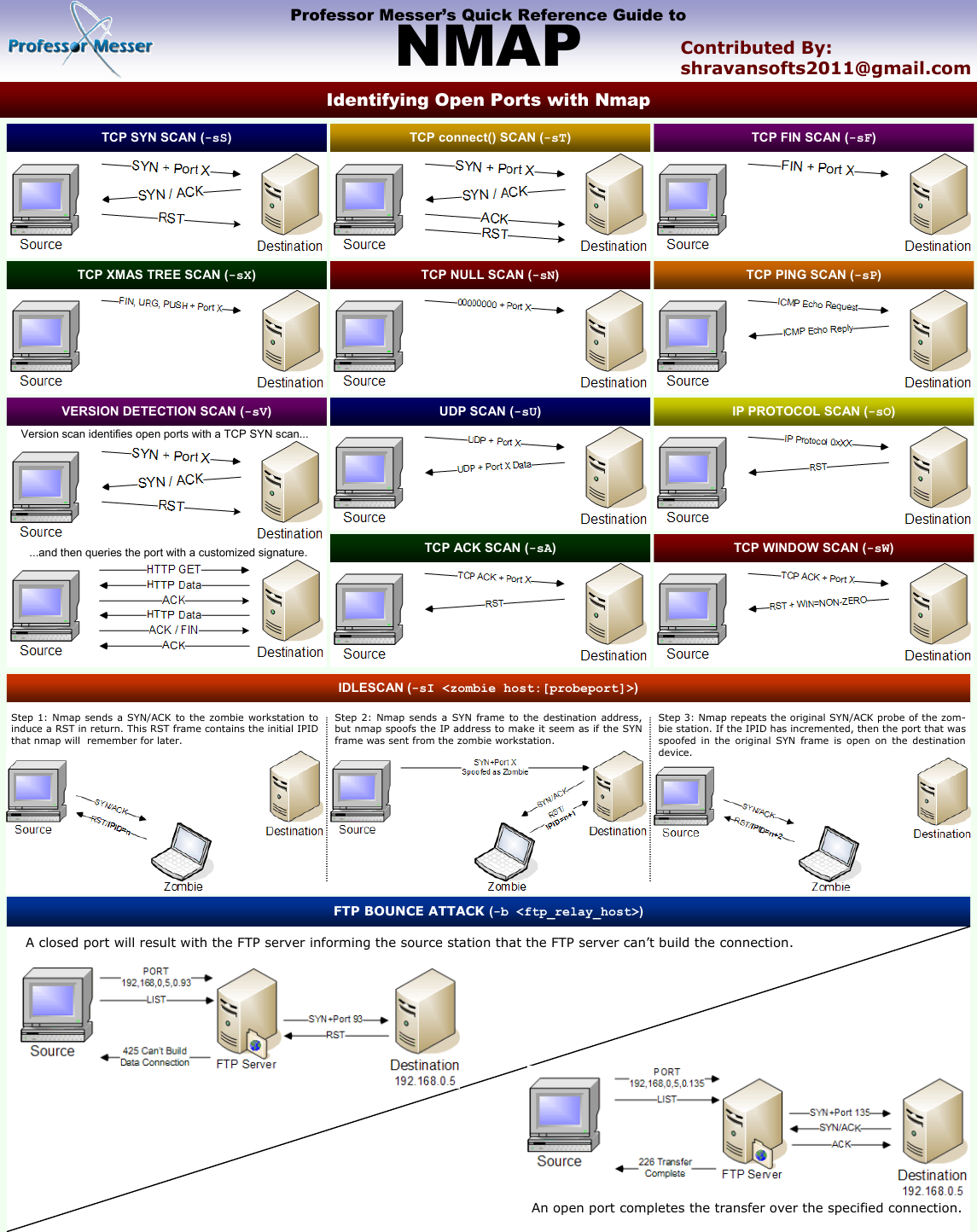
Nmap is a very extensive tool and has many possibilities, in CTF the command I use most is this one, and depending on the result I get, I perform other types of scans.
Once the scan is finished, it is saved in grepable format
This command performs a comprehensive scan, identifying open ports, service versions, and OS details of the target.
nmap -p- -sT -sV -A $IP
-p-: Scans all ports (1-65535).-sT: Performs a TCP scan (complete TCP connections).-sV: Tries to determine the version of services running on open ports.-A: Enables OS detection, version detection, and script scanning.$IP: The target IP address.
This command executes security scripts and vulnerability detection on open ports, providing detailed information about potential security issues.
nmap -p- -sC -sV $IP --open
-p-: Scans all ports (1-65535).-sC: Executes security scripts and vulnerability detection using Nmap's scripting engine.-sV: Tries to determine the version of services running on open ports.--open: Displays only open ports in the result.$IP: The target IP address.
This command focuses on running specific Nmap scripts designed to detect and assess vulnerabilities in services and systems on the target.
nmap -p- --script=vuln $IP
-p-: Scans all ports (1-65535).--script=vuln: Executes specific scripts related to vulnerabilities.$IP: The target IP address.
TCP Enumeration
UDP Enumeration
Certainly, here are the Nmap scripts separated:
Directory and file search:
Relevant information search:
SSH brute force:
DNS brute forcing:
Obtain a copy of the configuration from a poorly configured CMS:
Versions and possible vulnerabilities:
Enumerate users on SMB:
WordPress enumeration:
HeartBleed attack:
Banner grab:
Check if vulnerable to shellshock:
Port Scanning
Each one has its way of enumerating ports/services running under a system. I usually follow these steps.
Initial scan of open ports on the system
Service enumeration and versioning for discovered ports on the system
In case of having a slow initial scan, I usually apply the following variant
This scan does not encompass all ports, and we are probably skipping some interesting ones that escape this scan. In that case, we can go aggregating search ranges in order to determine the ports that are open (Since launching the -p- when nmap takes a long time tends to stop the scan making it incomplete):
In case of having an HTTP service running under a port, we can take advantage of the http-enum.nse script from nmap to enumerate directories and files of the web service (It has a small dictionary but it can serve us to have a quick overview of the hosted resources):
Visualization of categories for nmap scripts
These categories are all that nmap has, being able for example for an FTP or SMB service to apply the following categories:
Regarding the Low Hanging Fruit, interesting ports to look for in our initial scans can be the following (There are many more, but they correspond to services that can guarantee the execution of remote commands on the systems):
Regarding the FTP service, it is interesting to check if we can upload files. In case of having an IIS, if we see that we are able to host an asp/aspx file and point to it from the web service, we can establish a reverse TCP connection.